HACK.BAK System Requirements
HACK.BAK system requirements 2025 - can your PC run HACK.BAK?
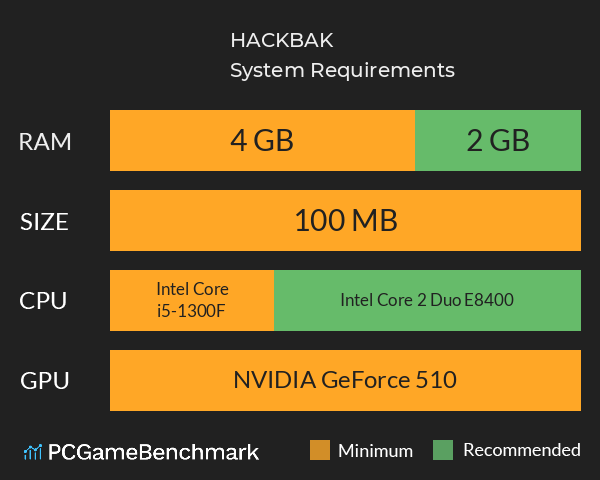
| Minimum | Recommended | |
| CPU | Intel Core i5-1300F | Intel Core 2 Duo E8400 |
| Graphics Card | NVIDIA GeForce 510 | NVIDIA GeForce 510 |
| RAM | 4 GB | 2 GB |
| File Size | 150 MB | Unknown |
| OS | Windows 11 | Unknown |
Can you run it? Test your computer against HACK.BAK system requirements.
Can I Run HACK.BAK?
In terms of game file size, you will need at least 150 MB of free disk space available. The cheapest graphics card you can play it on is an NVIDIA GeForce 510. An Intel Core i5-1300F CPU is required at a minimum to run HACK.BAK. However, the developers recommend a CPU greater or equal to an Intel Core 2 Duo E8400 to play the game. HACK.BAK system requirements state that you will need at least 4 GB of RAM. Additionally, the game developers recommend somewhere around 2 GB of RAM in your system.
HACK.BAK will run on PC system with Windows 11 and upwards.
Looking for an upgrade? See our graphics card comparison and CPU compare for benchmarks. We'll help you find the best deal for the right gear to run the game.
HACK.BAK FPS - what frame rate can you expect?
How many FPS will I get on HACK.BAK? An FPS Monitor is the first step in understanding how the parts in your gaming PC are actually performing in real-world conditions. It's the perfect way to track HACK.BAK FPS drops and stutters.
Download our free tool on Overwolf to count your frame rates as you play, and test how tweaks to your settings can boost FPS and increase HACK.BAK performance. Our app is compatible with hundreds of the best PC games and available now.